These aren’t normal times. All kids schooling from home. Restaurants aren’t open. Millions of people “sheltering in place.” I ‘visit’ my elderly dad in Frisco by parking in his driveway, dropping bags of groceries at the garage door, and then stepping back to my car like some kind of unseemly ‘drop’ from a TV drama.
Something that hascontinued as normal, however, in the course of business, is the work of responding to cybersecurity incidents and conducting workplace investigations. Companies are still having to defend against and respond to cybersecurity attacks, including data breaches. They’re also still having to conduct investigations and ensure regulatory compliance regarding all kinds of matters including discrimination claims, SEC matters, and theft of company data and trade secrets, to name a few.
The real question for professionals who fight these fights – information security folks, HR professionals, risk managers, in-house lawyers and others – and whose job is to protect their companies and their colleagues who work alongside them is how to do this important work in the time of COVID-19, when almost everyone is working from home? How do you protect your organization, when company resources are distracted and dispersed, leveraging unauthorized remote access tools to connect with confidential company systems and information, across insecure personal Wi-Fi and other less secure networks?
Let’s talk cybersecurity first. It’s important to know that cyberattackers are absolutely seeking to take advantage of the uncertainty and fear associated with COVID-19. For those of us who follow such things, every day brings news of a new phishingcampaign or watering hole attack designed to trick employees into handing over their company email and other credentials to threat actors. According to one recent report, phishing emails are up more than 600% since the end of February as cybercriminals look to leverage the COVID-19 pandemic.
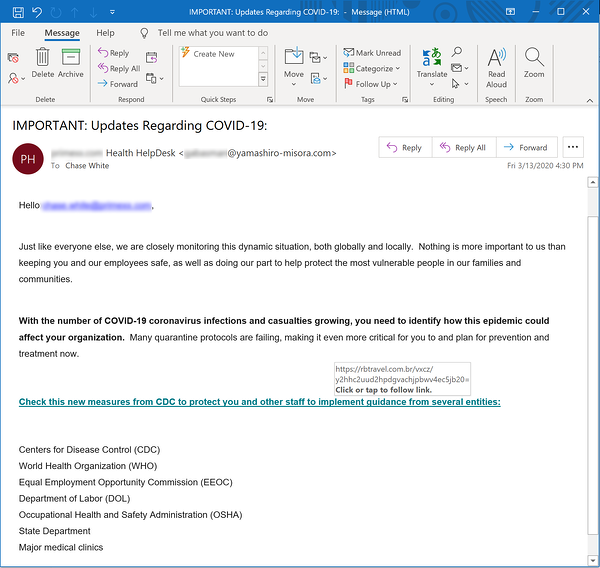
An example of a recent phishing email meant to trick employees
Additional challenges revolve around the unavailability of security resources – people who are out sick or simply distracted by child care and other obligations while working at home. Add to these risks those associated with an increased attack surface resulting from upward of 90% of an organization’s workforce suddenly being deployed remotely, and you have a perfect storm of bad guys doing bad things in an environment increasingly and significantly harder to protect.
Our experience also tells us that in these difficult times, we should expect to see an uptick in incidents requiring internal investigations. Following other seminal events in our history, including 9/11 and Hurricane Katrina, we saw a marked increase in behavior that required corporate investigation. We’re sure to see the same thing with COVID-19. And it won’t be easy. How do you interview people who aren’t in the office? How do you collect, image and analyze a laptop or a cellphone, when those devices are at someone’s house?
First and foremost, communication is key. Companies should be telling their employees who in the company will be communicating about COVID-19, so they know where to expect these messages to come from (and which messages to ignore). They should also be telling folks which external sources can be trusted, directing people to known and respected sites such as the CDC, Texas Health and Human Services and others.
And of course, as always, employees should be informed about the latest COVID-19 phishing campaigns going around – show them screenshots of scam emails so they can be on the lookout and resist the urge to click, accordingly. Companies that don’t communicate with their employees and arm them with the information they need to resist these attacks can expect those same folks to be easy pickings for cyberattackers, putting them and their employers at risk.
For technical folks, get in the trenches on your controls. Block unapproved third-party remote access tools, check capacity for the ones you’ve deployed, and validate all technical controls once you’re on the other side of your deployments. For all of us, there has been a rush to support a sudden mass migration of employees to work from home. Now is the time to go back and be sure nothing was missed in the mad dash, that no holes were left open for cyberattackers to exploit.
Also, and again on the other side of any recent large-scale adjustment of your workforce, some proactive measures are prudent, including tabletop exercises, threat hunts and the revision of critical protocols such as those concerning wire transfers and the movement of monies. This is the time to look for any indications of compromise in your network and to review, test and revise your defenses. Threat actors know companies are more vulnerable right now, and they are looking to take advantage.
Lastly, on the investigations side, even if you don’t have one currently in progress, anticipate your needs when the next investigation should arise in this new environment. Get a secure, remote interview process in place. Draft an investigations plan specific to COVID-19 and revise and adapt as needed. Expect some of your own needed personnel to be unavailable and develop alternative options. And remember to leverage a trusted partner in support of all this critical work – now is the time to connect with your outside law firm and your digital forensics provider to discuss how they are prepared to support your investigations in this new reality.
COVID-19 has changed our lives in ways not seen before. But companies still must resist and respond to cyberattack. They still must conduct investigations, ensure regulatory compliance and protect corporate assets. It will take creativity, innovation, collaboration and a commitment to mission to ensure success, however. Those who undertake these efforts will find their way, and they will avoid the pitfalls and challenges that lie ahead.
John Ansbach, J.D., CIPP-US, serves as vice president of engagement management at Stroz Friedberg, an Aon company in Dallas. He is a former general counsel and chief legal officer, and an expert in cybersecurity incident response and digital forensic investigation. For more information, he can be reached at john.ansbach@aon.com.
