Last week, the law offices of James T. Shelton in Clarendon, Texas, which is about 60 miles east of Amarillo, received a sudden and serious spike in calls.
In fact, the law firm, which specializes in advising on real estate, probate, wills and trusts, received several thousand calls, but not the kind they wanted.
Jim Shelton, the firm’s principal, says the calls came in from all over, including Canada and the United Kingdom. Folks were calling about an email they received concerning a “lawsuit subpoena” from Susie@jsheltonlaw,” which is a valid firm email address.
The trouble was, no one from the law firm sent the email. Even worse, the email contained a virus – a Word document attachment loaded with a malware payload that, according to Webopoedia, allows cybercriminals to “steal banking credentials and other personal information on a user’s system, ultimately allowing them to gain access to the financial records” of that user. The email address was valid and there is an employee of the firm named “Susie,” though the last name was fabricated in the email.

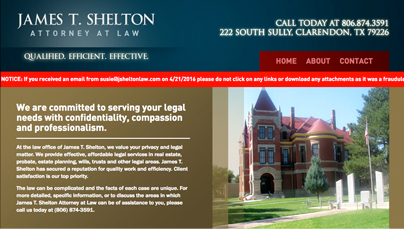
As soon as Mr. Shelton became aware of the problem, he contacted his email service provider and took action. The firm scanned their systems for any viruses. They found none. They also shut down the email account and placed a bright red banner on the website warning visitors who received the email not to “click on any links or download any attachments.” (See Illustration A, the website with the warning banner).
That’s the good news. The bad news is it’s hard to know how many people received the email – a type of attack known as phishing – and, of those, how many fell for the trick, opened the attachment and as a result unknowingly uploaded the virus.
This specific phishing email scam is particularly serious for two reasons: (1) the virus driven by the attachment targets sensitive banking and financial records; and, (2) the attackers socially engineered their attack, using a valid email address from a real person[1] at a real law firm based on the actual web domain of the firm.
The email also was recipient-specific; that is, the attackers apparently used mail merge or another tool to customize the email so that when an employee of ABC company received it, the subject read “ABC.com lawsuit subpoena,” further increasing the appearance of a legitimate email. (See illustration B, an actual email received during the attack.)
Making matters worse for lawyers is that legal departments were targeted. The email read, “Did ABC.com legal department get this? It is urgent.” As a result, unsuspecting email recipients were directed to forward the email (ostensibly about a “lawsuit subpoena”) to their legal departments and, not knowing any better, in-house counsel may well have opened the attached virus-containing Word document.
While these types of phishing email scams are certainly not new, they are increasingly more sophisticated. They are also expensive.
According to a report last year, “The extrapolated total annual cost of phishing for the average organization is more than $3.7 million,” including “productivity losses” that account for more than $1.8 million of that aggregate number. (Source: SC Magazine, “Report: Phishing costs average organization $3.7 million per year,” by Adam Greenberg, Senior Reporter, August 27, 2015).
With regard to the Shelton law firm phishing attack, companies and their employees are urged to be on the lookout for this email. Do not open it, do not open the attachment, and contact your IT department in the event an email like this one is received. Be sure to tell your IT folks about it and the virus it might contain, so they can conduct a safe examination.
Contact your IT folks also if you or someone in your company or firm did receive it and opened it – there may be actions that can be taken to ameliorate any damage, such as reimaging the hard drive.
More broadly, this attack shows just how important it is for lawyers to be ever vigilant about cybersecurity. Build, develop and nurture a culture in your organization that not only preaches that cybersecurity is everyone’s responsibility, but that also delivers training to give them the tools to help in the fight.
Cybercriminals aren’t going anywhere any time soon, but a vigilant, well-trained and prepared organization can at least help to level the playing field and make it harder for them to be successful.
John Ansbach is the General Counsel for General Datatech, L.P., a global technology solutions provider based in Dallas, Texas. He manages all of the legal affairs of the company and oversees the company’s information security efforts and its global operations program. He also writes on cyber security, which can be found at www.ansbachblog.com. Follow John on Twitter at @johnansbach and connect with him on LinkedIn at www.linkedin.com/in/johnansbach.
